A Firewall or the Cloud: Which is More Secure?
Table of Contents
If you’ve used the internet at all over the past few years, you’re probably aware of the ongoing cloud debate over security. Some say cloud-based solutions expose engineering intellectual property (IP) because it is outside the firewall. Some say that local software applications or on-premise are at more risk. After all, one of the biggest IP threats that a manufacturer faces is someone physically walking away with confidential information.
So let’s break it down. Ready for a discussion about security?
The Risk of Intellectual Property Loss
So why is this a big deal?
Well, it all comes down to the consequence of losing design IP. Some companies have invested heavily in the ability to manufacture products incredibly fast. That can be a significant advantage. However, by itself, without innovation in design, won’t win the marketplace. Such companies often occupy a fast follower position in the market, where they make copycat products once the original is launched.
Now, what would happen if such a company making copycat products got a hold of engineering models and documentation at design release? Well, that company would likely beat the original manufacturer that designed the product to market. Crazy as it sounds, it can happen. The copycat company would be first to market, capturing market share.
So this isn’t some whimsical issue. It affects revenue.
Secure behind the Firewall
For manufacturers, data is technically most secure behind a firewall. Unless the IT staff makes some grievous mistakes, bad external actors, in general, cannot penetrate this security approach.
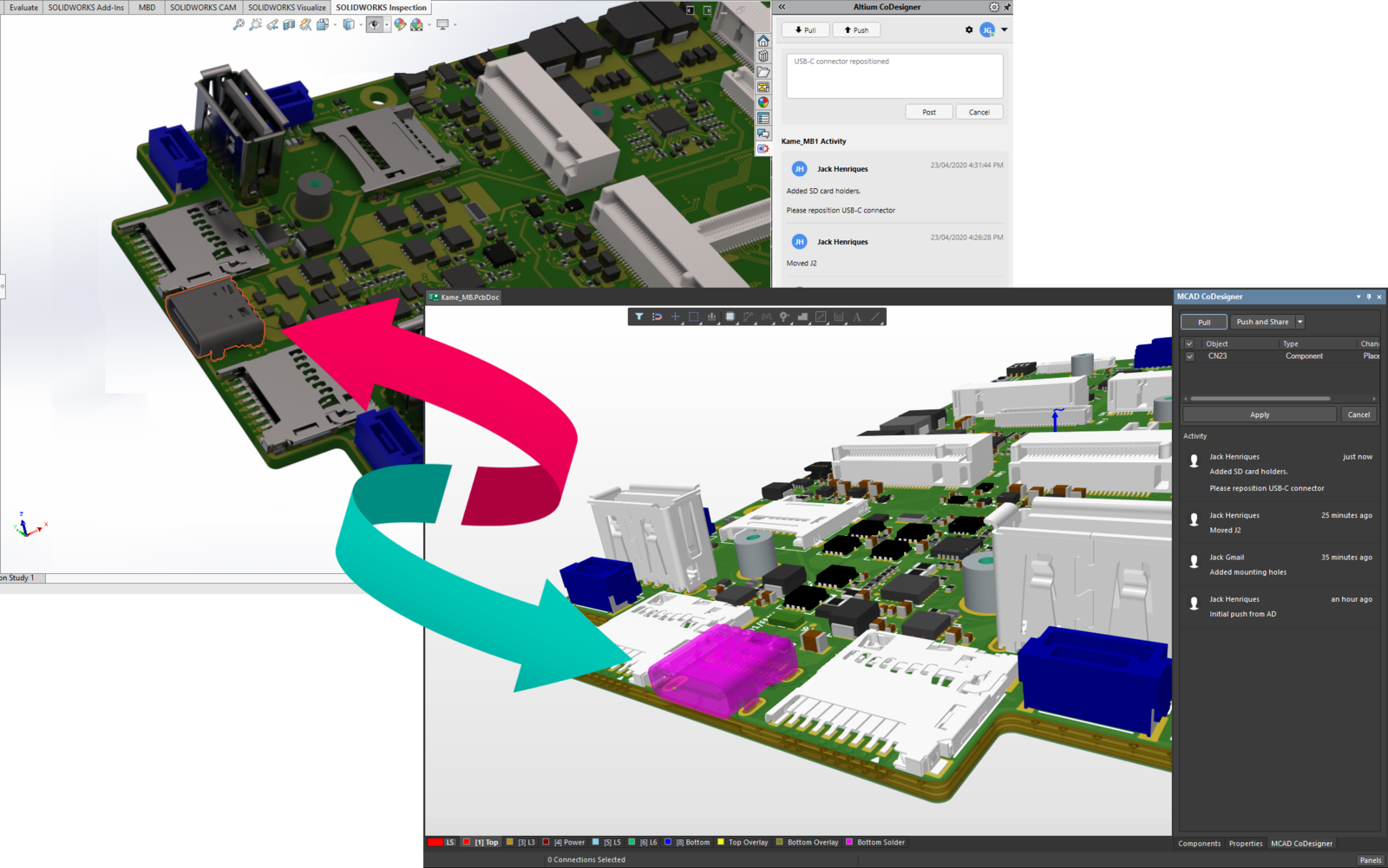
However, that’s not to say there isn’t a price. Collaborating externally around a firewall causes two separate behaviors. First, IT staff must develop painfully complex procedures to share data with external parties. This might include technical data packages that procurement uses for request-for-quote processes. Second, employees often circumvent those procedures when under extremely tight schedules with email attachments. Moreover, of course, nearly all companies use some cloud-based email service today.
Yes. Firewalls are technically more secure. However, frankly, they create costly process burdens or are frequently circumvented with email.
Secure in the Cloud
Some argue that the cloud is more secure. However, how does that work?
Cloud data is usually stored in an encrypted form, meaning that even if a hacker was able to access it, they couldn’t read or understand it. An individual can hold encryption keys, but the service providers frequently hold them instead. This is easier and more convenient, but less secure. Most cloud services give users extra options for security, such as an extra encryption step, but there’s no guarantee the data is entirely safe.
In addition to what happens to data in the cloud, it is essential to talk about competence. Microsoft spent $1 billion on security alone in 2017. Amazon likely spends nearly that much on security as well. These large cloud service providers are getting the best and the brightest security experts in the industry. That’s why some feel better with those experts on the job than the IT staff they can hire in their company.
From a practical perspective, cloud-based solutions foster better security practices. The process to share technical data packages with suppliers is more straightforward and faster than one done from behind a firewall. Those folks that would email attachments instead finding that sharing from a cloud-based solution is more natural and allows updates. When you have the right capabilities as incentives through a cloud solution, you drive better security behaviors.
Should You Move?
There was a time where on-premise data centers were indeed more secure, and it’s easy to get stuck in this mindset. In reality, though, employees circumvent those security protocols every day. The only way an on-premise data center is safer now would be a data center that is not connected to the internet at all.
So when considering this issue, think about a few things:
- Are your security protocols being circumvented today? Email is too easy. Schedules are too tight.
- What is your company’s security investment like today? Look at the security profile of the cloud platform for the solution. What is its investment in security?
- What is the importance of collaboration at different phases of your development process?
- Is your company encountering development problems, like respins and change orders, due to out-of-date information?
I think scrutinizing the answers to those four questions will lead you down the right path for you and your company.